When A Tesla Looks Like an Attacker
A case study in why anomaly detection isn't enough
I want to walk through a case where traditional anomaly detection and UEBA systems fall short.
A ton of unusual activity ends up being benign—and alerting on all of it creates massive noise for security teams.
Rather than speak in abstracts, I wanted to walk through a concrete example we saw that ticked all the usual boxes of “unusual”—but turned out to be completely benign.
Let’s dive in.
Some Logins That Looked Very Unusual
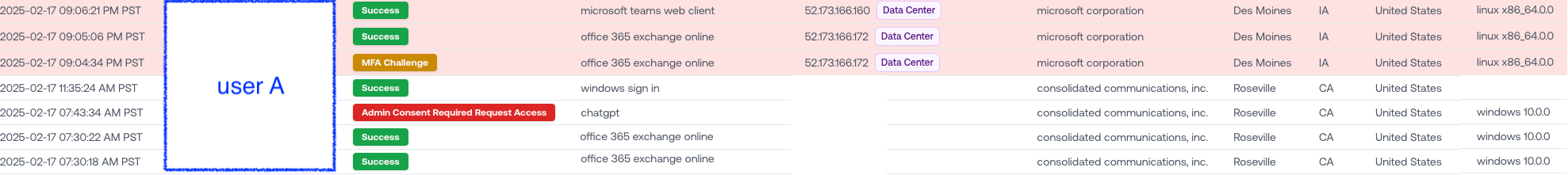
Here’s the login timeline for the user we were investigating:
These logins certainly check all the usual “suspicious” boxes:
The user is based in California
The login was from a Microsoft data center in Des Moines, Iowa
It happened at 9 PM local time, well after working hours
The device was a Linux machine
That’s already weird—this user normally logs in during business hours from a Windows machine in Roseville, CA.
So far, this looks like classic attacker behavior:
Threat actors often use cloud infrastructure like Microsoft and AWS data centers to blend in.
The time of day was off.
The OS was off.
The IP range was off.
Let’s dig deeper.
A Closer Look at Exchange Logs
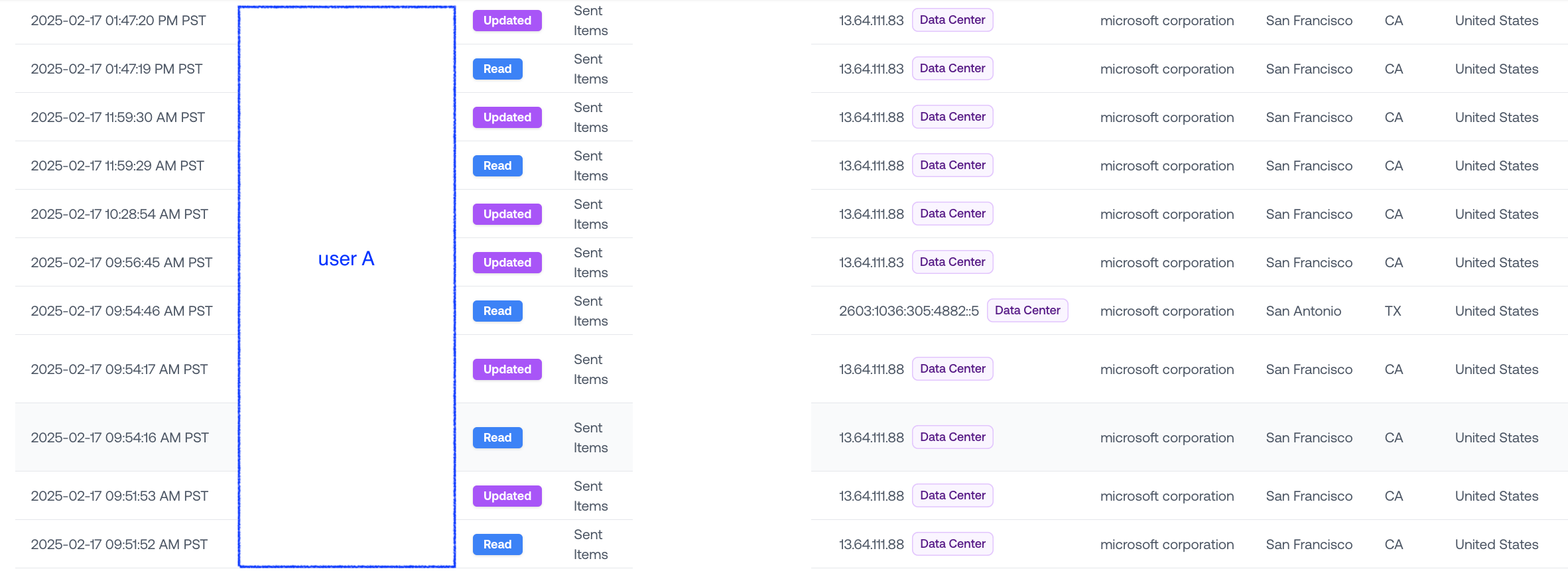
Here’s the Exchange activity for the user leading up to the suspicious logins (subjects hidden to maintain anonymity):
This user’s normal traffic usually comes from a Microsoft data center in San Francisco, which makes sense given their California location.
We’ve seen in past investigations that Microsoft will route user traffic to the nearest datacenter—though it’s not always predictable.
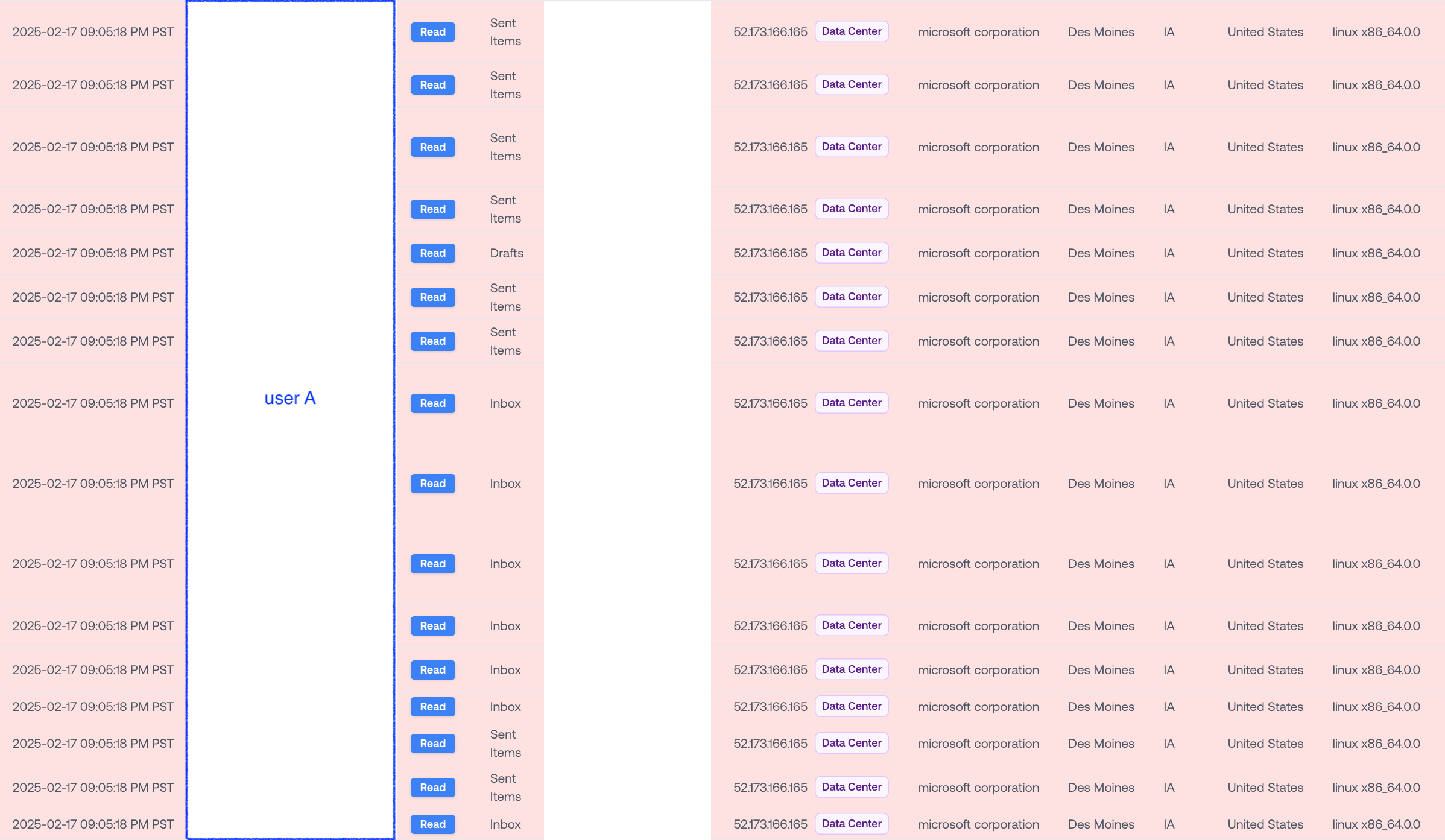
Here’s what the Exchange activity looked like right after the suspicious logins (subjects hidden to maintain anonymity):
Normally, this user’s Exchange traffic comes through Microsoft’s San Francisco datacenter.
Now we see a sudden detour to Iowa. Looks pretty suspicious, right?
This activity also appears to be programmatic: within 1 second, we see the user access emails in their Inbox, Drafts, and Sent Items back to back. Even more suspicious.
Between the logins and Exchange access, we also see many distinct IPs within the same subnet (52.173.166.0/24). That’s something we typically see happen during programmatic access.
Could This Be an Attack?
Let’s recap:
Unusual region (Des Moines)
Unfamiliar OS (Linux)
Late at night
Programmatic mailbox access
IP rotation within a Microsoft-owned subnet
Put together, it makes for a pretty compelling argument that this is an attack:
Maybe this is an attacker logging in from an Azure-hosted proxy.
Maybe they’re using a toolkit that pulls inbox data for staging a phishing campaign.
Maybe this is the early stages of a BEC.
But, actually this case wasn’t any of that. In fact, it was actually completely benign activity.
The Real Explanation: Tesla
Turns out, this user had logged into their mailbox through their Tesla's dashboard console.
With this newfound information, let’s review the evidence:
Why Des Moines? Tesla likely relays requests through an Azure-hosted backend that lives in a Microsoft datacenter in Iowa.
Why Linux? The Tesla OS is Linux-based.
Why programmatic access? The Tesla system likely pulls in a snapshot of the inbox all at once to show emails on the dashboard.
Why the late hour? Possibly scheduled syncs or polling behavior by the console's background services. User’s probably driving in their car at night.
Takeaway: Anomaly ≠ Attack
This is a textbook case for why traditional anomaly detection is not sufficient to do high fidelity threat detection.
Sure, all this behavior looked unusual for this user… and it was. They don’t usually use their Tesla to check their emails. That doesn’t mean it’s an attack though.
This particular edge case is just one of many. If your detection logic is built on statistical deviation or UEBA, you'll end up drowning in false positives.
What actually works is combining anomaly signals with deep context about attacker behavior. For example, if you want to see a real attack laundered through Microsoft infrastructure, and the deep context involved, check out our deep dive here.
And if you also care about stopping these attacks, reach out and I’ll share more about the system we’ve built to do so at Petra.