How Attackers Launder Phishing Emails Through Microsoft Infrastructure
Attackers often use hacked accounts to "OneDrive Phish" other companies. This allows them to launder their phishing emails through Microsoft infrastructure. So, how can we detect and stop them?
Every Attacker Has Two Goals.
No matter the organization attacked, no matter the attacker, an attacker only ever has two goals:
Extract $ from the compromised organization.
Use the compromised organization to attack OTHER organizations.
We see #2 extremely frequently in BEC incidents.
For the attacker, there are two huge advantages to weaponizing a compromised account for further phishing:
Hacking is about trust. If you can send emails from a trusted organization, getting a user to click on a link is much easier.
Emails from a trusted organization are much more likely to bypass inbox spam/phishing detection.
The way we see this occur most often in the wild is via OneDrive phishing. People expect to receive OneDrive links from known collaborators.
But there’s actually a third huge advantage to OneDrive phishing: you can launder all this activity through Microsoft’s infrastructure.
Previously: How Attackers Phish with OneDrive (and How it Appears in the Logs)
In a recent post, we walked through how attackers set up OneDrive phishing lures using a compromised account, and how you can use the SharePoint logs to catch it.
This time, we’re looking at the emails attackers send — and the tactics they use to make these emails blend into normal user activity.
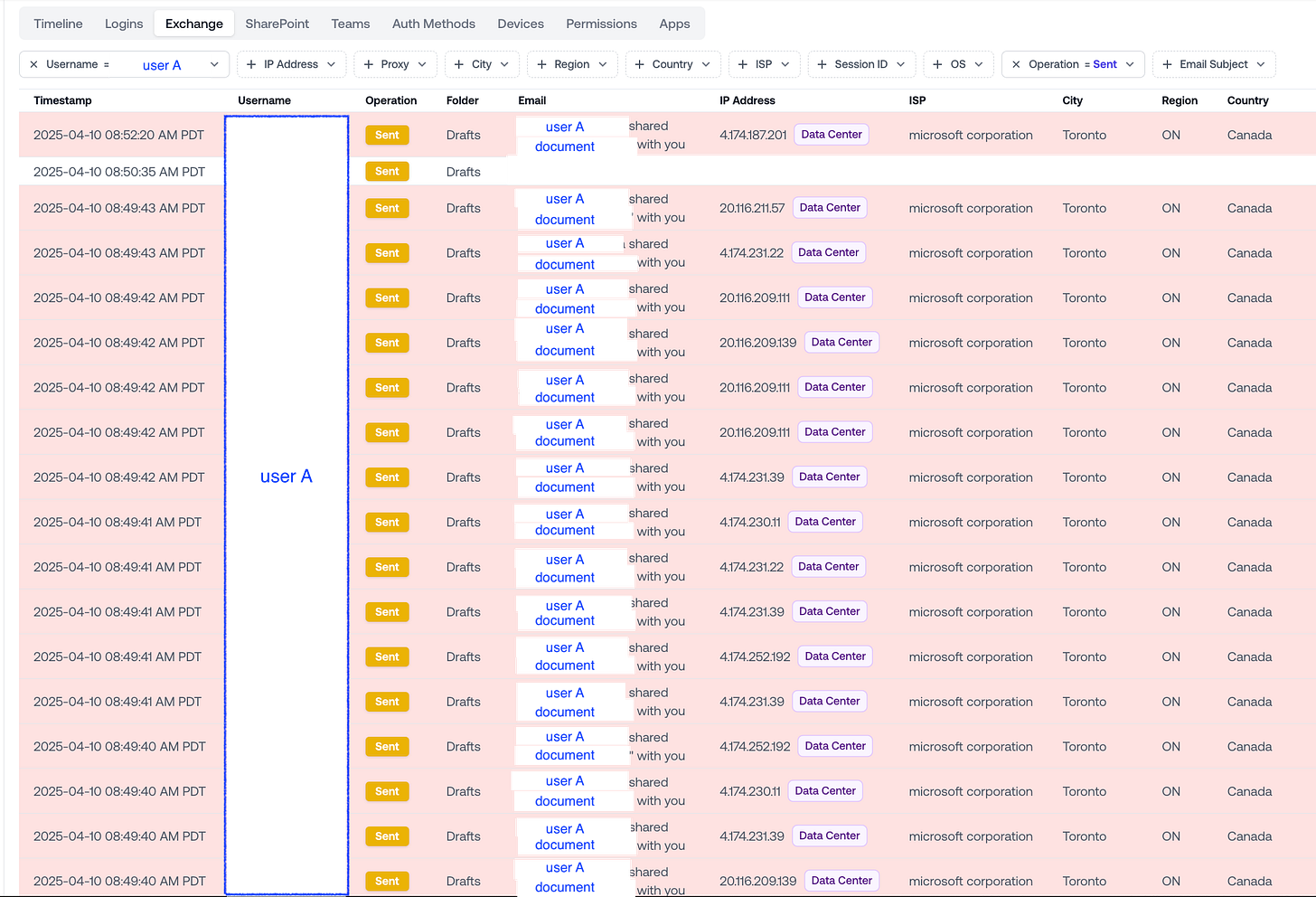
Example: A Flurry of Phishing Emails, All Laundered Through Microsoft IPs
Here, an attacker has successfully hacked an account and is weaponizing it to launch a OneDrive phishing campaign.
This is what we see in the Exchange logs:
A flurry of Send events––all within a few seconds.
All sent from the hacked user’s account.
Requests routed through a wide range of Microsoft IPs, all from Toronto.
If you just look at these logs and try to figure out which behavior came from the user and which came from the attacker, you don’t have a lot to go off of.
You can’t tie the IP, the ISP, the City, the Region, or the Country to the attacker. All the traffic is routed through generic Microsoft data centers.
Legitimate user traffic also often passes through Microsoft data centers, so when both the phishing and regular activity come from Microsoft-owned IPs, it’s hard to tell the difference.
This is why attackers have so much success with lateral OneDrive phishing: it’s extremely difficult to detect because so many of the logs come from Microsoft infrastructure.
Recap: Why Is a OneDrive Phishing Attack so Effective?
1. Takes advantage of existing trust.
If you’re used to getting files from Brad Smith through OneDrive, you don’t question another OneDrive link. If anything, you're more likely to click.
2. Dodges email defenses.
These emails aren’t from sketchy domains—they’re from real M365 accounts using real OneDrive links.
Often, the compromised user has shared files with the victim before, so this behavior doesn’t even deviate from their baseline.
3. Launders activity through Microsoft’s infrastructure.
Just like SharePoint logs, Exchange logs for these messages come from Microsoft data center IPs—not the attacker’s.
To make matters worse, a lot of benign user activity also comes through these same Microsoft IPs—making it tough to distinguish attacker behavior from normal usage.
So, How Can You Detect This?
You could flag when a large amount of emails are sent by an account in quick succession, but that’s too little, too late. And, it’s easy for an attacker to just space these operations out long enough to evade detections.
So, you’ve got to catch it before.
The best way to do this is to build a deep behavioral baseline for the user’s Exchange, SharePoint, Teams, and login activity. Use variations from this baseline as an indicator that something’s off.
Not all the signals in the Exchange/SharePoint logs go through Microsoft data centers. If you’re vigilant, you can catch signs of an attacker hiding in these logs. Just beware of red herrings (like impossible travel that’s not really impossible travel).
Takeaway: Hard But Not Impossible.
These campaigns succeed not just because of clever lures—but because of how well they blend in with real traffic.
As attackers continue to level up, there’s rarely a single log entry that screams “malicious.” The attacker reveals themselves through subtle signals across SharePoint, Exchange, and login data.
Spotting the bad guy requires stitching those signals together.
That’s what we built Petra Security to do—calculate deep baselines of attacker/user activity and correlate attacker activity across Exchange, SharePoint, Teams, and more.
If you see these attacks on your Microsoft tenants and want to level up your defenses, reach out to me on LinkedIn. Happy to swap notes and help.