What's up with all that Impossible Travel in SharePoint?
Differentiating between real IPs and Microsoft datacenters in SharePoint logs. Hugely important for incident investigations.
A couple of my recent deep dives have focused on Entra ID logs and Exchange logs.
Sharepoint logs, though, are a goldmine - they’re just as important when it comes to monitoring M365 environments.
But, you’ve got to sift through an interesting source of noise: many of the IPs listed in the ClientIP field are Microsoft datacenter IPs instead of the end user’s IP.
So, where’s the SharePoint activity really coming from?
Let’s dive into some examples.
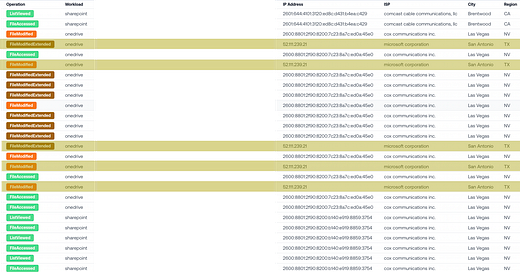
Example 1: User Based in Las Vegas
This is Sharepoint activity for a user based in Las Vegas.
All of the access events (File Accessed, List Viewed) come from the true IP for the user, in Vegas.
However, all the modification events (File Modified, File Modified Extended) events are mixed between the user’s true IP in Vegas and a Microsoft datacenter IP in San Antonio.
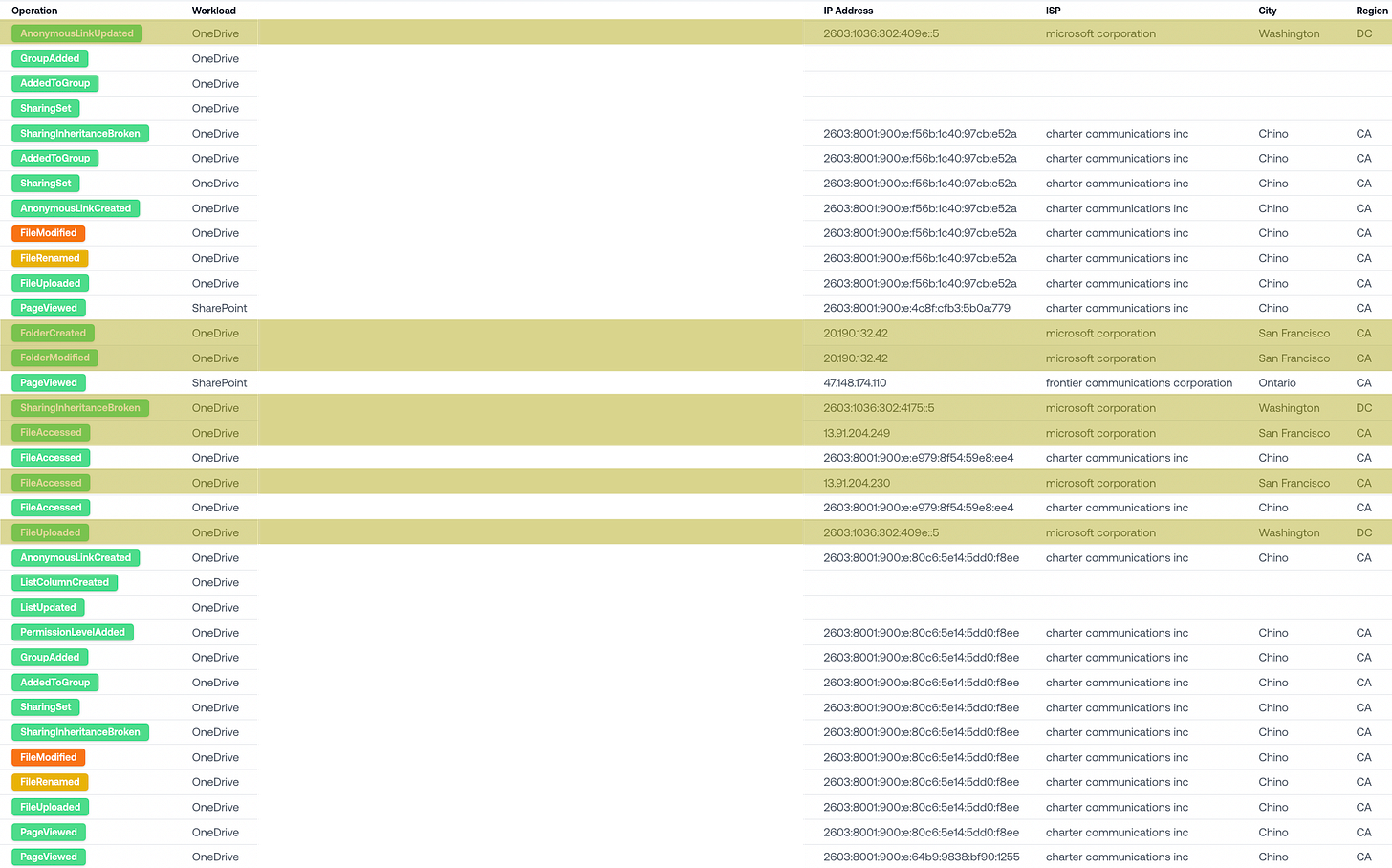
Example 2: User Based in California
Here’s another user based in Chino, California (near LA).
In their SharePoint logs, we see likely true IPs from Chino, but also Microsoft datacenter IPs from San Francisco and DC.
For this user, it looks like many operation types (FileUploaded, FileAccessed, FolderCreated, FolderModified) are coming through the Microsoft IPs. But, there doesn’t seem to be a clear pattern.
The San Francisco Microsoft datacenter at least makes sense, given its geographical proximity to Chino.
Why is some traffic routed through the DC Microsoft datacenter? I have no idea.
Example 3: User Based in Australia
With this third user, once again, we see many different SharePoint operations coming from Microsoft IPs.
Just like in the previous case, there doesn’t seem to be any consistency on which Microsoft datacenter the operations get routed through.
Some logs route through a datacenter in New South Wales (close to the user), other logs route through a datacenter in Washington (across the ocean).
What Is Going On?
I dug into the Microsoft docs to try and better understand this behavior. Here’s what I found:
“For some services, the value displayed in this property might be the IP address for a trusted application (for example, Office on the web apps) calling into the service on behalf of a user and not the IP address of the device used by person who performed the activity.”
Here’s a concrete example: if someone is modifying a spreadsheet saved in Sharepoint using the Excel web app, we could see Sharepoint activity coming from both the end user and from the Excel web app.
That activity from the Excel web app is likely what’s getting routed through Microsoft IPs.
Takeaway: Beware of Microsoft Datacenter IPs When Attributing Behavior to a User.
When you’re doing forensic work with Sharepoint logs, remember that the activity often gets routed through Microsoft IPs, which can make it harder to trace the origin.
Some logs come through the user’s true IP.
Others come through a Microsoft datacenter close to the user.
Still others come through a Microsoft datacenter hundreds or thousands of miles away.
There are, thankfully, quite a few other clues in these logs that help us piece together whether particular Sharepoint activity came from the real user or the bad guy.
If you’re interested in this research, reach out - always happy to talk about it.
Until next time,
Adithya