New Password Spray Campaign Using Residential Proxies
A stealthy password spray campaign is using Virginia-based residential proxies. Here’s what we’re seeing and how to block it.
Campaign Snapshot
Several months ago, we dove into a widespread, stealthy password spray campaign originating from a data center in Mexico.
Now we’re tracking a new campaign—and it’s even stealthier.
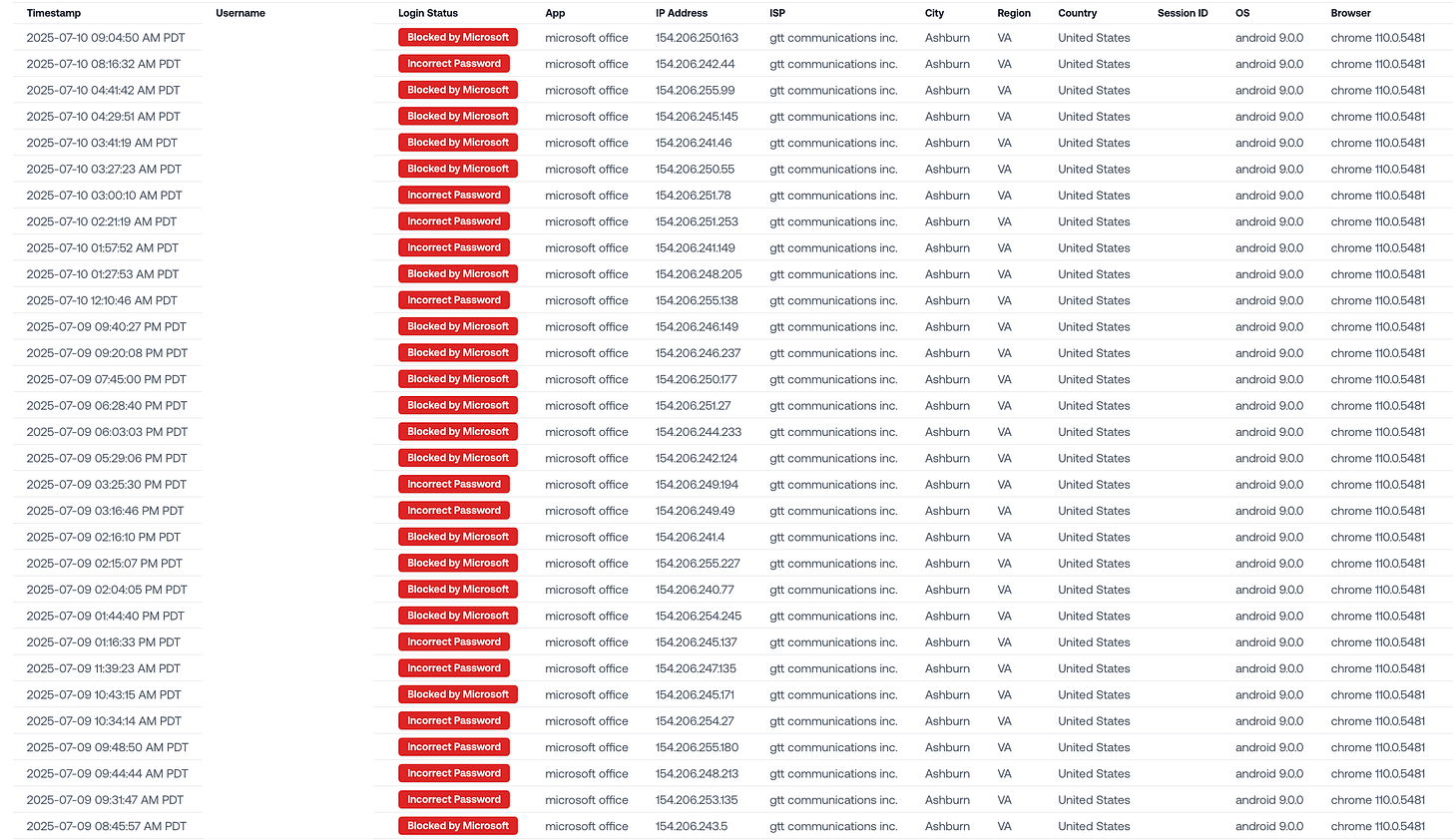
First observed: May 30, 2025.
The malicious login attempts use a tight cluster of IPs in Ashburn, Virginia:
154.206.240.0/20(AS3257 GTT Communications Inc.)154.208.64.0/21(AS3257 GTT Communications Inc.)154.208.112.0/21(AS3257 GTT Communications Inc.)
They all have an outdated user agent: microsoft office + android 9.0.0 + chrome 110.0.5481
How to Block these IP Ranges
We recommend blocking this campaign by hardcoding malicious IP ranges instead of relying on geolocation.
For more details on how to block this IP range with conditional access, check out our previous blog here.
Quick copy‑paste:
154.206.240.0/20,154.208.64.0/21,154.208.112.0/21
The Rise of Residential Proxies
While these IPs aren’t labeled as VPNs and proxies by most IP enrichment providers, further digging reveals that they all belong to the SOAX_PROXY network.
SOAX and similar services aggregate traffic from real consumer devices—often via SDKs embedded in mobile apps—then lease that egress bandwidth to customers. That means:
Requests appear to come from residential or mobile ISPs rather than obvious data centers.
IP reputation looks “normal.”
User‑agent strings frequently inherit stale or odd mobile fingerprints (explaining the old Android + Chrome combo we’re seeing).
This is part of a broader trend: attackers are increasingly using residential proxies to evade detection.
What’s causing this? The massive demand for large‑scale web scraping—fuel for today’s data‑hungry AI models—has slashed the cost of residential proxies and made them plug‑and‑play.
And opportunistic attackers are happy to take advantage.
Takeaway: Stealth is the Name of the Game
Residential proxies are only half the story. This campaign is carefully designed to fly under the radar in other ways too.
Across affected tenants:
~90% of targeted users see fewer than 10 attempts per month
Most tenants experience light, distributed probing (< 50 total users targeted)
Put together, each failure looks like a routine fat‑finger—unless you’re carefully monitoring attack patterns across tenants.
If you’re managing M365 environments, remember to block these IP ranges:
154.206.240.0/20, 154.208.64.0/21, 154.208.112.0/21
And if you’re exploring how to use adaptive detections to stay ahead of these rapidly evolving attacks, connect with me on LinkedIn or reach out at [first name] [at] petrasecurity.com.