How Did Singapore Bypass Your US-Only Conditional Access?
When Microsoft's faulty geolocation makes your security controls fail silently
I was recently helping a customer investigate a false positive from a competing solution. The alert was triggered by an employee who forgot to report their travel to Southeast Asia.
During this investigation, I discovered something fascinating.
This tenant had blocked non-US logins, but the employee successfully logged in from Asia. How?!
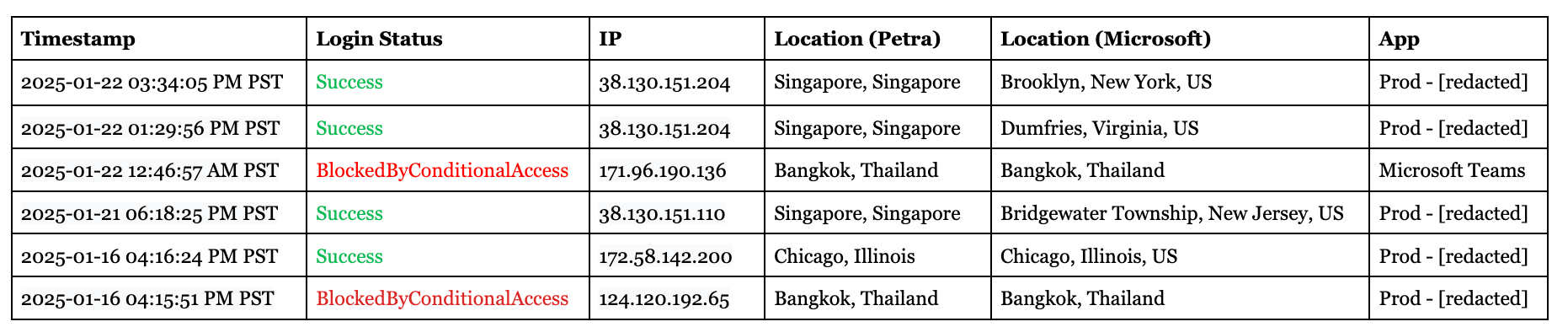
Here are the logs so you can see for yourself:
Microsoft's geolocation service misidentified the Singapore logins as originating from the Eastern Seaboard (New York, New Jersey, Virginia).
Since logins from the US were allowed under the conditional access policy, these logins weren’t blocked…
Most people understandably assume that location-based conditional access policies are enough to secure their M365 environments. The truth is, these policies aren’t perfect, and when they fail, you’re none the wiser.
Any Microsoft admin without a third-party monitoring solution would have never even known that logins had happened from outside the US.
Consider this your reminder to use conditional access as one piece in a layered security strategy for your M365 environments.
If you’re looking for a more reliable way to determine IP geolocations when looking at Microsoft alerts, shoot me an email at [first name] [at] petrasecurity.com. Happy to trade notes.