Corporate Espionage in the Cloud
The quiet side of BEC: how attackers exfiltrate data without leaving a trace
BEC Isn't Always Loud
When most defenders hear the term BEC, they typically imagine the following sequence of events:
Attacker compromises an email account.
Attacker uses account to send out fake invoices or more phishing emails to collaborators.
Attacker uses inbox rules to hide activity from real user.
But, this isn’t always the case. Sometimes, attackers are after sensitive data.
E-mail is the backbone on which many businesses are run. A single employee’s mailbox often contains sensitive IP, memos about internal strategy, and attachments with proprietary documents. And attackers know this.
That’s why nation state actors like Void Blizzard love targeting M365 accounts.
When attackers are after data, they’re not loud at all. They slip in, grab what they need, and vanish without a trace:
No suspicious emails sent to other accounts.
No inbox rules.
No suspicious app registrations.
We recently detected an attacker conducting corporate espionage. The attacker was only in the user’s mailbox for 10 seconds.
Let’s dive into the case.
Note: all identifying details in this case have been anonymized, but the relative timeline of the attacker’s activity has been preserved.
A 10 Second Break-In
We caught this one while running a retrospective health check for a tenant in the oil and gas industry.
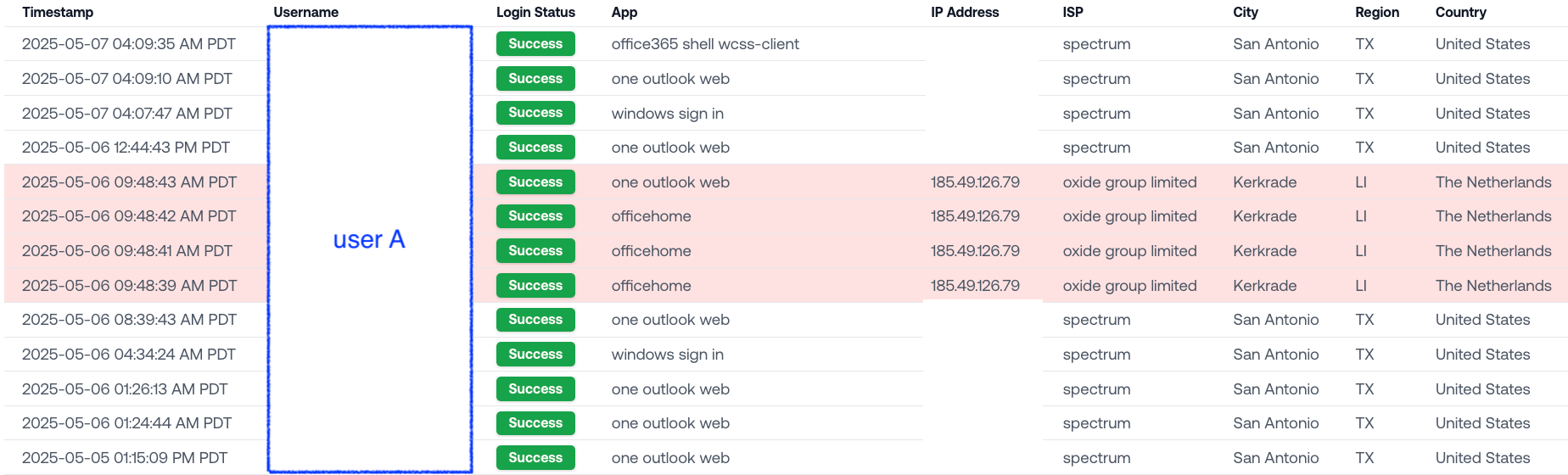
The user in question was based in Texas. Here are the logins:
At 9:48 AM PDT, we see four quick logins from an IP in the Netherlands. The ISP is oxide group limited - this IP turned out to be a remote desktop.
This is textbook impossible travel, but it’s stealthy:
No failed logins from previous attempts to compromise the account.
No obviously suspicious proxy networks or VPNs.
No prolonged period of suspicious logins - all the malicious logins happened within a 4 second timespan.
Let’s take a look at the user’s Exchange mailbox logs (subjects are anonymized):
Within 10 seconds of logging in, the attacker rapidly accesses emails containing sensitive information and trade secrets:
Engineering and modeling output
Internal review workflows
Project milestone updates
This is what a programmatic, targeted search looks like. All the mail access happened in a single second, and looked through emails from up to a year ago. The attacker got in, swept the mailbox for the information they were looking for, and got out.
Takeaway: Quick, Quiet, and Clinical.
This attacker was quick, quiet, and clinical. Here’s what makes attacks like this so dangerous:
Attackers can take seconds. Forget hours or even minutes—this compromise took 10 seconds flat. Well-resourced attackers can move fast, particularly in the age of programmatic toolkits.
They leave almost no trace. No inbox rule. No phishing emails. Nothing that would trigger a traditional BEC detection. The only way to catch this is to monitor logins and mail access in real time.
They could’ve come back months later. Microsoft session tokens can last a long time. That means the attacker could’ve waited months before quietly returning to steal more data using their live session—and no new login events would appear in the logs.
Stealthy is the name of the game. Without the ability to stitch together subtle login and Exchange signals in real time, you’re flying blind.
If you’re a defender looking to reliably detect these types of stealthy attacks, drop me a note on LinkedIn.